Exploring Microsoft’s Advanced Threat Protection Technologies-Sooner You Know Better
Microsoft has been working on developing the layout of the security technology at an accelerated pace for quite some time. This acceleration is since Microsoft has come up with the adoption of various services such as Windows 10, Office 365, as well as Azure. The advanced features mainly work on the core IT environment. They not only secure the network through protection but display the various cycles of events during the attack. However, there is a lot of confusion that encircles these technologies. This includes ATP (Advanced Threat Protection), which is itself a unique technology, but people do not have a clear idea about it. So, follow this blog with rapt attention to learn about ATP technologies and all the things they will offer.
Three Main ATP Technologies
Now, it is time to get a clear idea about Microsoft ATP technologies and what this technology will provide for all the customers.
- Microsoft Defender Advanced Threat Protection.
- Azure Advanced Threat Protection
- Office 365 Advanced Threat Protection
Microsoft Defender Advanced Threat Protection
This technology always works on the endpoints, mostly on the desktop services and the Windows servers. It has Windows 10, and it needs the policy to activate this on Windows 7. This requires the deployment of the agent software. Microsoft has made the main aim of MDATP on Windows 10 quite clear. It is equipped with the on-the-down-level operating system to enable total coverage during the transmission to Windows 10. MDATP mainly aims to provide an Endpoint Detection and Response Area (EDR).
MDATP comes with complete control of the endpoints and aims to identify known malicious activities. The entire capability is done based on the intelligence with the help of Microsoft Security Graph. It is updated as per the latest AI and Machine Learning know-how.
It is equipped with an automated investigation that moves out to several endpoints to track the activity of the various malware. This minimizes the investigation time and helps you to know the root cause seamlessly.
Azure Advanced Threat Protection
This ATP technology mainly focuses on safeguarding your identities. It is a cloud-based solution that is equipped with some inbuilt components that are used to analyze information that comes from the Active Directory domain controllers. It is equipped with Microsoft Security Graph, which signifies that it benefits from security telemetry and intelligence.
This will send you alert signals if there is a typical attack technique like passing the hash or passing the ticket. These are mainly used by the attackers to move laterally inside your organization. Azure helps you to take control of the user activities. This helps you to analyze the detailed activity models which portray the normal behavior of the user. If the workings take place outside of the typical scenario, then the alerts will come out for further investigation. Azure ATP comes with the User and Entity Behavioural Analytics area. Microsoft comes with new detections to Azure ATP because of the evolution of the latest malicious techniques.
Office 365 Advanced Threat Protection
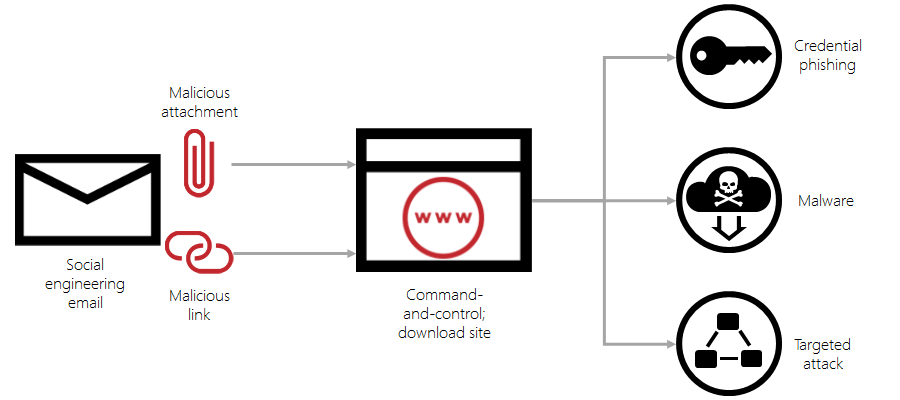
This is a threat protection technology that helps to safeguard emails as well as other confidential data that is present inside Office 365, such as SharePoint Online, OneDrive for Business, etc. It helps to give zero-day protection against the attack of the malware. It works through the analysis of files inside a detonation chamber to find out the behavior of the data when the user opens it. If there is any suspicious activity, it will straightaway block the file.
It can restrict the user to the vulnerability of the malicious URLs or web links associated with email or documents. The entire idea is achieved by providing a database of malicious sites. If the link turns out to be spiteful, it will restrict the end-user from coming to the main area. Apart from this, Office 365 will go through all the files added by these links in a similar manner.
Office 365 is equipped with features that restrict phishing attacks. It comes with machine learning models to know and find out who you like to communicate with. This is meant for the identification of phishing attempts. Phishing attacks are increasing at an alarming rate. This will be quite effective for the end-user to provide the credentials or other related data. Protection is needed to reduce the risk is an essential aspect of the strategy.
Computer Solutions East comes with all the software-related services that help you to strengthen your business without any hassle. It has partnered with Microsoft, so all the latest technologies will be there in your hands. So, it is time to collaborate with Computer Solutions East to resolve all your IT-related issues. The best services will be available at your convenience.
Call us to learn more!


