
Cloud Computing for Small Businesses
Cloud computing is a modern approach to managing and processing data through remote servers hosted on the internet, which provides …
Top app security solutions to drive business growth by ensuring holistic application safety that keeps vulnerabilities at bay.





Security is becoming a bigger concern for business decision-makers regarding the apps they develop, purchase, and deploy. In reality, 95% of respondents believe that third-party protection validation is an important consideration when purchasing software.
We’re dedicated to helping you gain a competitive edge through safe apps. You can quickly demonstrate the safety of your software and development processes with Veracode, reducing the sales cycle and customer confidence.
In our state-of-the-art Customer Innovation Center, we accelerate the maturity of your network security initiatives by providing leading technology technologies, consulting and implementation services, and personalized testing. Our experts will help you assess your existing capabilities, reduce tension between humanitarian and defense teams, and implement the tools required to secure applications from malicious use.
Organizations are increasingly turning to SaaS applications for their flexibility and cost savings, but they often discover that they lack the requisite visibility and control levels. CSE experts provide a cloud-native subscription service that provides visibility, enforcement, data security, and threat protection for an organization’s cloud-based services.
Application spy agencies secure sensitive business software from unauthorized access and manipulation and viruses and other cyberattacks. Application protection providers help businesses protect their apps through steps like the application review process, application code review, and secure app creation. If security bugs are found during the analysis, these companies will make recommendations for fixes and collaborate with in-house developers to improve security across all platforms. Vulnerability evaluation is a common part of application protection, and many cybersecurity companies provide it as part of their regular procedures.
Your applications and workers need Internet access to succeed in today’s connected business world. Mobile devices, which are doubly appealing to hackers for business and personal data, are increasingly being used to gain access.
CSE assists you in determining your present and future web use criteria. It then provides you with the layered security defense you need to combat today’s most dangerous threats. Basic security success factors around passwords, network segmentation, and security-rich software creation will secure businesses and users alike.
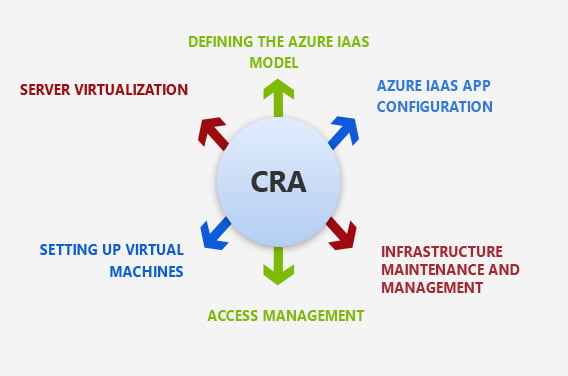

Assists in the establishment of an application development protection program to encourage the creation of security-focused applications.

In the software development lifecycle, secure software development training establishes a solid application security experience baseline.

Container security assessment, solution design, implementation, and managed services

Improve the security infrastructure and posture enables a threat-driven stable software development strategy.

Detects code-level flaws, run-time security flaws, and logic flaws in apps.

DevSecOps transformation and deployment, including individuals, procedures, and tooling

Web-based community applications profit from centralized security. Streamline the security of system vulnerabilities and gain clear insight to respond to threats quickly.
With the ever-changing threats, you’ll need a company to assist you with all aspects of application security. For many years, we’ve been helping our clients secure their applications consistently. We use tried methods and algorithms to provide you with safe solutions with our world-class application testing solutions.
Professionals have accurate ideas to get the company to its newest height and are well aware of businesses globally. Our experts regularly upgrade their expertise to stay tuned to the latest technology glitches and threats and thus guarantee quality safety for all your applications.
Application protection refers to how a company protects its sensitive data from outside threats by maintaining all applications used to operate the company, whether developed internally, purchased, or downloaded. Application security aids in detecting, correcting and preventing security flaws in every kind of software application, but almost every application has flaws. At least one vulnerability rated as one of the top ten web vulnerability categories was found in roughly 70% of all applications. Commercial applications, investment banking software, and government-written software are all vulnerable.
Our cloud solutions help the global enterprise achieve business goals.

We work to identify the clients IT problem and offer the best solution. Time and again,we face a situation that demands agility and the right set of talent that can solve technology issues.
Learn More
Not all projects are about innovation. Some are those that add a feather in our cap no matter what we deliver and how. It was typically a government project that involved a lot of roadblocks right.
Learn More
Being an expert IT solutions partner in the US and worldwide, we are committed to delivering results that drive business growth. Our team recently worked with Neil Hoosier & Associates to resolve.
Learn More
Cloud computing is a modern approach to managing and processing data through remote servers hosted on the internet, which provides …

Technology has been transforming businesses ever since the invention of the wheel. However, in recent years, the business landscape has …
Continue reading “Azure Secrets: The Key to Secure & Automated Cloud Workflows”

Effective communication is important for the success of any team. But with so many options, choosing the right platform can …
Continue reading “Choosing the Right Collaboration Tool: Microsoft Teams vs. Slack”

Cloud computing services allow businesses to undergo digital transformation, which can enhance efficiency and reduce expenses. Choosing the most suitable …
Continue reading “A Guide to Managed Cloud Computing Services”