
Cloud Computing for Small Businesses
Cloud computing is a modern approach to managing and processing data through remote servers hosted on the internet, which provides …

Custom software development is the process of designing, creating, deploying and maintaining software for a specific set of users.




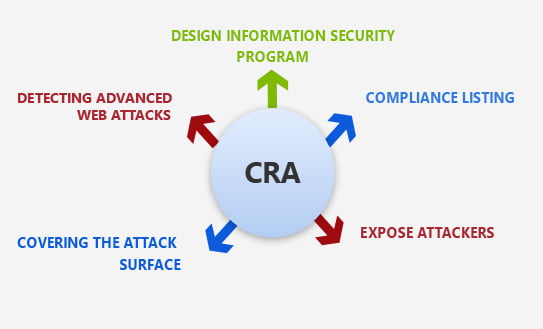
Information Security Assessments analyze the maturity of your information security program and identify gaps, weaknesses, and opportunities for improvement. Expert services deliver the Computer Security Management (CISO) experience that provides you with the wide range of expertise needed for incident response, compliance and the latest threat intelligence to address information security flaws and implement actionable mitigation strategies. Next, expose attackers as they move across layers: attackers can use any layer of your stack to gain access, build footholds, and move laterally within your system. Full-stack visibility helps us to spot a move so that you can disrupt the attack — before it’s too late. Cover more of your growing attack surface-inherit vulnerabilities as you use commercial and open source tools like Joomla, WordPress, Magento, PHP, and ASP.NET. So we’re investing in proprietary research and threat intelligence to understand these vulnerabilities, exploits, and attacks. And then the experts will detect advanced web attacks. You add your vulnerabilities, such as those in the OWASP Top 10, when rapid development cycles leave little time to implement and test secure coding and configuration. Advanced detection analytics techniques, including machine learning and anomaly detection, provide our experts and industry-leading tools for detecting stealthy attacks such as SQL injection.

Selected information security specialists track, triage and intensify the most important threats continuously

Our information security experts repeat attacks to check whether they can be better avoided, detected and remedied.

Our experts are checking the identification and blocking logic of signatures, rules and compliance measures and applying it continuously.

They build and train algorithms with data scientists to identify sophisticated, multifunctional threats.

Researchers search for shifts in the environment of attacks and identify the latest developments

Our professional cybersecurity specialist can collaborate with various hosting and network partners.

The CSE experts offer accredited cybersecurity training programs
To safeguard the company, we provide end-to-end consulting, security, and monitoring services. To help you identify your security perimeter, priorities, and procedures, we advise on your information security approaches based on your current level of maturity. Our information security systems are secured and we track the network so that information-attacks are identified and responded in advance. End-to-end advocacy, safety, and security management systems defend the digital business from cyber threats and internal malicious behavior.
Our cloud solutions help the global enterprise achieve business goals.

We work to identify the clients IT problem and offer the best solution. Time and again,we face a situation that demands agility and the right set of talent that can solve technology issues.
Learn More
Not all projects are about innovation. Some are those that add a feather in our cap no matter what we deliver and how. It was typically a government project that involved a lot of roadblocks right.
Learn More
Being an expert IT solutions partner in the US and worldwide, we are committed to delivering results that drive business growth. Our team recently worked with Neil Hoosier & Associates to resolve.
Learn More
Cloud computing is a modern approach to managing and processing data through remote servers hosted on the internet, which provides …

Technology has been transforming businesses ever since the invention of the wheel. However, in recent years, the business landscape has …
Continue reading “Azure Secrets: The Key to Secure & Automated Cloud Workflows”

Effective communication is important for the success of any team. But with so many options, choosing the right platform can …
Continue reading “Choosing the Right Collaboration Tool: Microsoft Teams vs. Slack”

Cloud computing services allow businesses to undergo digital transformation, which can enhance efficiency and reduce expenses. Choosing the most suitable …
Continue reading “A Guide to Managed Cloud Computing Services”