
Cloud Computing for Small Businesses
Cloud computing is a modern approach to managing and processing data through remote servers hosted on the internet, which provides …

Microsoft 365 Baseline process is all about breaking down the complex structure and simplify it.





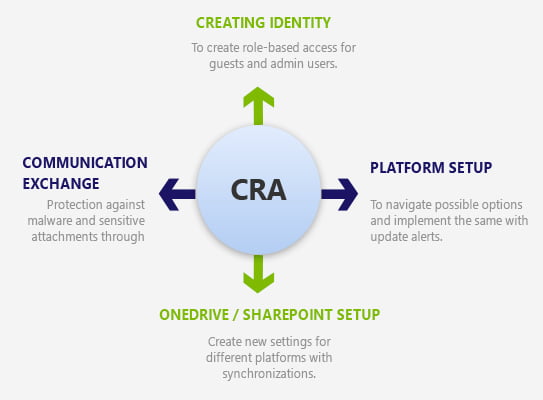
Our step-by-step CIS-enabled Microsoft 365 Security Baseline process is all about breaking down the complex structure and simplify it. We start the Baseline shift with creating the Identity by enabling admins, guests, and users with Multifactor authentication. Also, our M365 Baseline experts perform tasks to set up a break glass process and account that takes us to create the custom O365 login-page. The next step is to configure the Platform by setting up the DLP rules that follow GDPR compliance in a test-drive mode. In this step, we define the protocols that block certain aspects of the apps in Azure to enable using specific admin-accounts.
We then use step into creating OneDrive/SharePoint account with the ability to share default links to a specific set of people and restricting the non-owned items to them. OneDrive synchronization across multiple-connected domains assists users in adding apps to a newly created SharePoint site. The last step involves the Exchange of information through email forwarding and blocking any of those having malware-sensitive attachments. Once done, users can begin leveraging baseline features for Office 365.

Our office expertise helps in configuring advance threat protection for all baseline services

We protect Baseline on Azure as well with a pervasive AIP plan.

Our engineers can you the best out of your disk drives through AES-enabled Bit locker.

Leverage dedicated mobile team to systematically register mobile users through MDM certification.

Team aids in creating and implementing policy for a group of devices.

Assigning 2-factor authentication for Baseline applications.

Configuring OneDrive and Migrating users.
Our Microsoft-certified experts follow the benchmarks published by the Center for Internet Security (CIS) for Azure, Windows 10, Microsoft 365 Foundations, and Windows Server 2016. Leverage our experts’ prescriptive guidance for Microsoft 365 security baseline configuration.
Computer Solutions East stands as a recognized Microsoft partner following the best IT security practices that help organizations limit their data vulnerability and protect it against any persistent attack. Start creating a streamlined Baseline foundation to utilize Microsoft 365 for businesses with ensured dual levels of security settings.
Our cloud solutions help the global enterprise achieve business goals.

We work to identify the clients IT problem and offer the best solution. Time and again,we face a situation that demands agility and the right set of talent that can solve technology issues.
Learn More
Not all projects are about innovation. Some are those that add a feather in our cap no matter what we deliver and how. It was typically a government project that involved a lot of roadblocks right.
Learn More
Being an expert IT solutions partner in the US and worldwide, we are committed to delivering results that drive business growth. Our team recently worked with Neil Hoosier & Associates to resolve.
Learn More
Cloud computing is a modern approach to managing and processing data through remote servers hosted on the internet, which provides …

Technology has been transforming businesses ever since the invention of the wheel. However, in recent years, the business landscape has …
Continue reading “Azure Secrets: The Key to Secure & Automated Cloud Workflows”

Effective communication is important for the success of any team. But with so many options, choosing the right platform can …
Continue reading “Choosing the Right Collaboration Tool: Microsoft Teams vs. Slack”

Cloud computing services allow businesses to undergo digital transformation, which can enhance efficiency and reduce expenses. Choosing the most suitable …
Continue reading “A Guide to Managed Cloud Computing Services”