
Cloud Computing for Small Businesses
Cloud computing is a modern approach to managing and processing data through remote servers hosted on the internet, which provides …

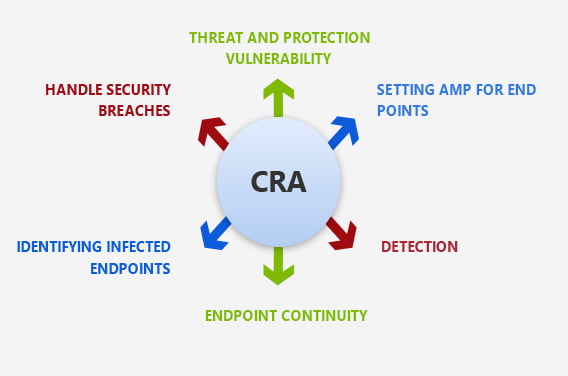
Advanced Malware Protection (AMP) for Endpoints intermix prevention, detection, and response capabilities in a single solution, leveraging the power of cloud-based analytics.





Advanced Malware Protection’s first step is to eliminate threats and potential vulnerabilities. Stopping threats early on guarantees minimum damage to endpoints and decreased downtimes after a violation. AMP for Endpoints uses a comprehensive range of protective technologies in real-time to avoid malware from targeting much of the time. Then we also start detection. While malware prevention techniques essential for a complete security solution for the next-generation endpoint, the battle against advanced threats needs additional steps. AMP for Endpoints tracks endpoints continuously so that new and unknown hazards are identified. Answer As there are that numbers and numerous advanced threats to slip past protection, the chance of infringement should be viewed as an eventuality. In this context, a robust toolkit should be implemented to detect infected endpoints and the extent of an attack. AMP for Endpoints provides granular endpoint visibility and intervention tools for addressing safety violations rapidly and efficiently combined with various prevention and detection capabilities. This offers a lattice of detection capabilities in conjunction with big data analytics to monitor files and traffic continuously on endpoints to determine if advanced malware is present.
Our experts keep looking for malicious artifacts in almost real-time to speed up the threat hunt.

Monitor disk space, memory and other objects of IT operations.

On request or schedule, you can check your endpoints for threat indicators.

We bring reliably and efficiently find the root cause of the incident.

CSE experts keep monitoring the file for any suspicious behavior and tracks its behavior when a suspected file reaches a user's network.

Cisco AMP tracks the traffic of the network and identifies any potentially unauthorized transactions or access points.

Your query results can be saved in the cloud or sent to other applications, such as Cisco Threat Response.
Cisco, a leading IT company, offers endpoint security to a range of customers in various areas. CSE partnership with Cisco has all our staff exposed to in their job roles and related activities. We make incorporating AMP quickly into simplifying business activities. Our Advanced Malware Protection CSE works on predefined AMP threat grid intelligence feeds are the most extensive collection of information for the industry with the broadest exposure in terms of real-time bouts.
Our cloud solutions help the global enterprise achieve business goals.

We work to identify the clients IT problem and offer the best solution. Time and again,we face a situation that demands agility and the right set of talent that can solve technology issues.
Learn More
Not all projects are about innovation. Some are those that add a feather in our cap no matter what we deliver and how. It was typically a government project that involved a lot of roadblocks right.
Learn More
Being an expert IT solutions partner in the US and worldwide, we are committed to delivering results that drive business growth. Our team recently worked with Neil Hoosier & Associates to resolve.
Learn More
Cloud computing is a modern approach to managing and processing data through remote servers hosted on the internet, which provides …

Technology has been transforming businesses ever since the invention of the wheel. However, in recent years, the business landscape has …
Continue reading “Azure Secrets: The Key to Secure & Automated Cloud Workflows”

Effective communication is important for the success of any team. But with so many options, choosing the right platform can …
Continue reading “Choosing the Right Collaboration Tool: Microsoft Teams vs. Slack”

Cloud computing services allow businesses to undergo digital transformation, which can enhance efficiency and reduce expenses. Choosing the most suitable …
Continue reading “A Guide to Managed Cloud Computing Services”